A lot of people running a homelab with a webserver, mailserver and more things, know the usage of a reverse proxy. In case you don’t, it is a nice solution to your port forwarding issues when it comes to reaching websites on more than one server behind one external IP address.
Technically you can do a lot more with a reverse proxy, but for this blog it is about websites only.
In this scenario you had to choose port 443 and 80 for your webserver and other webGUIs on other servers needed to run on alternative ports.
With the reverse proxy you can reach all of your webGUIs and websites on the different servers behind one IP address by using a name-based redirection. Just make some entries in your hosted DNS-panel for every website you want to reach, pointing to your IP address and the reverse proxy will do the rest.
It starts with the router
In my case I use the DSL router in bridged mode, which means that I use a different solution for routing/firewalling than the standard hardware which comes with my cable provider. Mostly on cable you are bound to hardware which might limit your needs. But in any case you will be using the port forwarding option the same way.
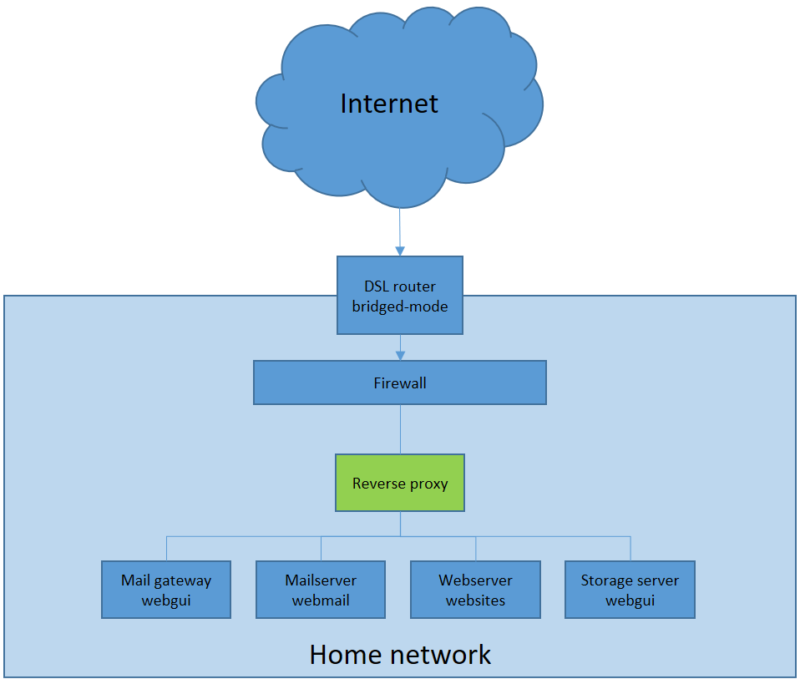
Name based redirection
So we have setup a reverse proxy (on the bottom of this article I will provide some links with the information how to build one), and now it is time to use the port forwarding function of your router/firewall to redirect ports 443 and 80 to the proxy.
As an example I made a basic graphical view how it setup at my homelab.
Notice that port 587 is going directly to the mailserver and port 25 straight to the mail gateway. Yes, you could even manage traffic to IMAP, POP3 and such with a reverse proxy, but I’m only using one mailserver, there has to be limit somewhere… When a visitor of www.mydomain.com enters the reverse proxy, it will detect the domainname and redirect the traffic to the webserver. If the visitor reaches nextcloud.mydomain.com, it will redirect this traffic to the nextcloud server and so on.
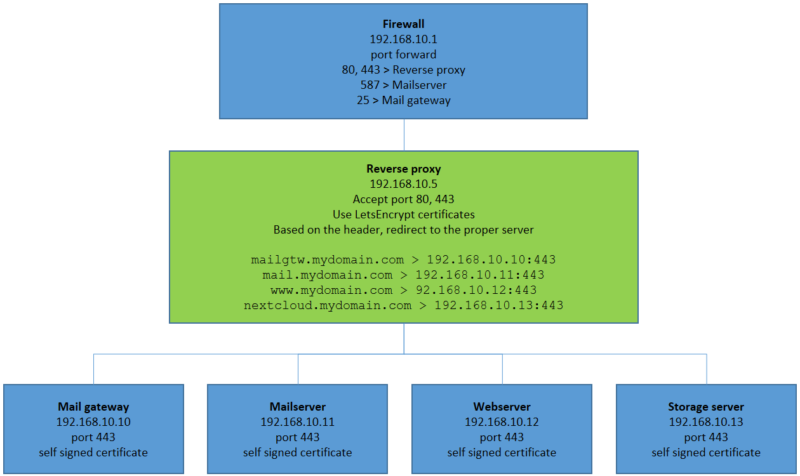
Single point managing SSL certificates
To make use of SSL certificates I use LetsEncrypt, which makes it easy to reach every server/website on HTTPS. With the proper setup you can have multiple websites handled by the reverse proxy, all with their own certificate.
You will need to use HTTPS on your target servers too, but in this case I use self signed certificates for 3652 days so the next 10 years I don’t need to refresh them… Ofcourse these servers probably are rebuild before that time anyway.

Leave a Reply